Notice
Recent Posts
Recent Comments
Link
| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
Tags
- IAM
- AWS 자격증
- 네트워크
- SAA
- DNS
- EC2
- vmware
- Firewall
- Troubleshooting
- GNS3
- ELB
- aws cloud shcool 8
- vyos
- aws SAA-c03
- Kubernetes
- NAT
- SAA-C03
- docker
- aws cloud school
- aws iam
- FTP
- AWS
- aws cloud
- linux
- Ebs
- tftp
- load balancer
- EC2 인스턴스
- aws saa
- ALB
Archives
- Today
- Total
나의 공부기록
[VMware] 18-2. VPN - Server to Client VPN 실습 본문
문제
VPN Server의 외부 인터페이스를 211.183.3.150/24와 내부 인터페이스 eth1은 10.20.31.150/24로 하여 비슷하게(=18-1 실습과 비슷하게) 구성 후, 잘 되는지 테스트하시오.
[조건]
pre-shared-secret : ah
ID/PW : aws /cloud
실습

1. VyOS 서버 설정
vyos@vyos#set int eth eth0 address 211.183.3.150/24
vyos@vyos#set system gateway-address 211.183.3.2
vyos@vyos#set service ssh port 22
vyos@vyos#commit
2. eth1 추가
- NIC 추가 - 물리적 연결


- eth1 IP 설정 - 논리적 연결
vyos@vyos# set int eth eth1 address 10.20.31.150/24
[edit]
vyos@vyos# commit
[ interfaces ethernet eth1 duplex auto ]
Cannot get current device settings: Operation not supported
not setting autoneg
[edit]- eth1 설정 확인
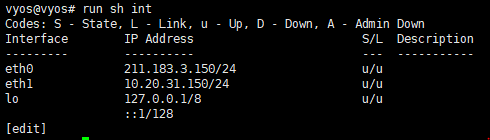
3. VPN 설정
3-1. IPSec 설정
vyos@vyos# set vpn ipsec ipsec-interfaces interface eth0
[edit]
vyos@vyos# set vpn ipsec nat-traversal enable
[edit]
vyos@vyos# set vpn ipsec nat-networks allowed-network 0.0.0.0/0
[edit]
3-2. L2TP 설정
# ip 부여 범위
vyos@vyos# set vpn l2tp remote-access client-ip-pool start 10.20.31.200
[edit]
vyos@vyos# set vpn l2tp remote-access client-ip-pool stop 10.20.31.210
[edit]
# ipsec authentication
vyos@vyos# set vpn l2tp remote-access ipsec-settings authentication mode pre-shared-secret
[edit]
vyos@vyos# set vpn l2tp remote-access ipsec-settings authentication pre-shared-secret ah
[edit]
vyos@vyos# set vpn l2tp remote-access authentication mode local
[edit]
vyos@vyos# set vpn l2tp remote-access authentication local-users username aws password cloud
[edit]
vyos@vyos# set vpn l2tp remote-access outside-address 211.183.3.150
[edit]
vyos@vyos# commit
[edit]
4. VPN Client 설정
- network-manager-l2tp-gnome 패키지 설치
- VPN 설정
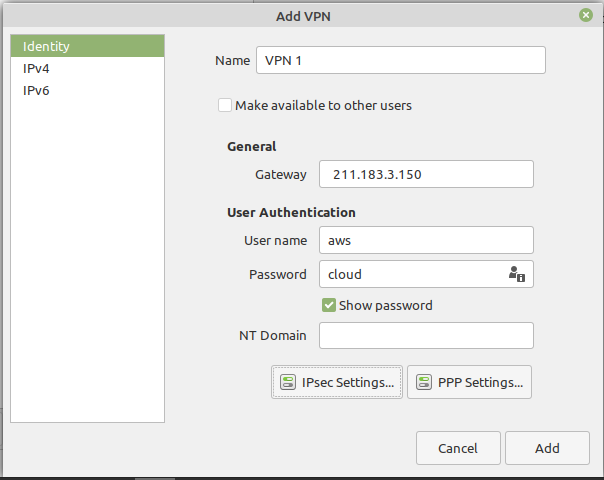

- VPN 설정 완료
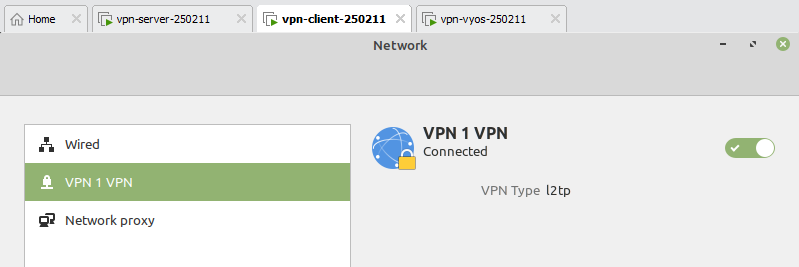
- 가상 인터페이스

5. VPN 설정 확인

'CS > Linux' 카테고리의 다른 글
| [VMware] 20. KVM(Kernel-based Virtual Machine) (1) | 2025.02.15 |
|---|---|
| [VMware] 19-1. VPN - Site to Site VPN (0) | 2025.02.14 |
| [VMware] 18-1. VPN - Server to Client VPN (0) | 2025.02.11 |
| [VMware] 17. VyOS Firewall 과제_심화 (0) | 2025.02.10 |
| [VMware] 16-2. VyOS Firewall 과제 (0) | 2025.02.10 |





